Background
Secure digital (SD) is a proprietary non-volatile memory card format that was developed by the SD Association (SDA) for use in portable devices. The SDA was established in 2000 by three main companies which set industry standards for SD cards. Today SDA has approximately 900 member companies involved in the design and development of SD standards. To display one of the trademark logos on a card, a company must adhere to all specifications defined in the SD Standard. Former specifications permitted the optional use of a password lock/unlock feature identified as CMD42, however, more recent specifications have made this feature mandatory.

CMD42
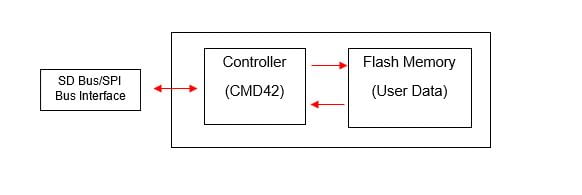
CMD42 enables the host system to use a 16-byte (maximum length) password to lock/unlock SD, microSD, miniSD, and eMMC devices. eMMC devices are not always part of the SD standard but most contain the CMD42 locking mechanism. This locking mechanism, when implemented using the proper commands (CMD42) prevents unauthorized access to the data on the device. The commands are transmitted between the host and the controller over an SD/SPI bus depending on the hardware implementation. By default, no password is set. CMD42 Locking is very rarely used in commercial devices so most cards in the wild are and remain unlocked. In fact, hosts running Windows, OSX and Linux operating systems do not implement the CMD42 feature set by default and do not check for CMD42 lock status when a device is plugged in. Further to that most USB to SD controller hardware (think of a USB to SD card reader) contain their own limited (No CMD42 support) mass storage device implementation and do not allow a host to communicate with the SD/eMMC controller directly. So, if a host does not or cannot communicate with the SD/eMMC controller directly and exchange CMD42 messages, a locked device may not show up at all as a block device, or appear as corrupt beyond repair because the host cannot see, or for that matter read or write to the block device.
Relevance to Digital Forensics
A common forensic workflow when dealing with media is to seize the evidence, image it, analyze it and then report on it. Most standard hardware platforms that run the forensic software (Windows, OSX or Linux) are not configured to run CMD42 and some do not have SD/SPI bus interfaces at all. Because of the host computers limitations, a forensic investigator won’t be able to detect the possible use of CMD42 or even acquire the data for forensic analysis. If a host bus can support direct SD/SPI commands, it may require kernel modifications and special utilities to execute the required commands.
CMD42 locking often has commercial purposes. A couple common examples of its use are blocking access to firmware in vehicles infotainment systems, in mobile and IOT devices to protect user data for privacy reasons.
More sophisticated criminals could even use this function to hide their data from law enforcement. If a device is CMD42 locked, then it can’t be imaged. Without being able to detect if a device is CMD42 locked, investigators may presume the device has hardware damage and could overlook potential evidence and intelligence.
Though the CMD42 function is not commonly used, it provides users, whether legitimate or not, with a method to instantly secure data without using disk encryption.
The Covert Forensic Imaging Device (CFID) includes the ability to IDENTIFY, LOCK and UNLOCK SD/uSD and eMMC cards using the locking mechanism discussed above, thus allowing forensic investigators and operators to detect and deal with CMD42 locked devices.
Conclusion
Though the CMD42 function is not commonly used, it provides users, whether legitimate or not, with a method to instantly secure data without using disk encryption.
The Covert Forensic Imaging Device (CFID) will include the ability to IDENTIFY, LOCK and UNLOCK SD/uSD and eMMC cards using the locking mechanism discussed above, thus allowing forensic investigators and operators to detect and deal with CMD42 locked devices.
References
DEFCON-27-Nicolas-Oberli-Poking-the-S-in-SD-cards.pdf
Micron Technical Note – TN-SD-01:Enabling SD/uSD Card Lock/Unlock in Linux Introduction
TOSHIBA_SD Card_Specification.pdf
www.sdcard.org

